ICMP and DDoS Attacks: A Medical Center Case Study
“Cybersecurity is not just about
technology, It’s about the people who use it. It’s important to create a
culture of security where everyone understands the risks and takes
responsibility for protecting themselves and their organization.” - Stephania
Mango
Working in cybersecurity at St. Gabriel’s Medical Center, I’ve seen firsthand how critical network reliability is in supporting healthcare operations. One recent incident underscored this importance. When medical center staff were unable to access the records server, our team faced an urgent issue: core medical operations were suddenly disrupted, affecting everything from patient records to timely diagnostics.
As a Network Engineer, I was responsible for investigating the issue, diagnosing the problem, and implementing an immediate solution to restore the center's functionality. What began as a routine network check quickly escalated when I realized I couldn’t remotely access the server.
Diagnosing the Network Issue
The records server at St. Gabriel’s Medical Center is the backbone of our digital infrastructure, supporting staff, physicians, and patient interactions with sensitive, real-time data. Any interruption in access could not only delay essential care but also pose a serious threat to patients’ health and privacy. Realizing the potential impact, I launched a preliminary Wireshark packet capture to analyze network traffic patterns. It was then that I noticed unusual spikes in traffic, suggesting a possible Distributed Denial of Service (DDoS) attack.
Figure 1.0: Client-Server Schema at St.Gabriel's Medical Center
Background: ICMP and DDoS
ICMP:
Internet Control Message
Protocol, an integral part of the
Internet Protocol Suite (TCP/IP) and operating at the Network Layer (Layer 3)
of the OSI model provides a mechanism for network devices (e.g., routers and
hosts) to communicate with each other for diagnosing network connectivity issues.
Devices can transmit control messages and error reports using the ICMP.
Moreover, ICMP is made to manage a wide range of situations, including
controlling network congestion, reporting problems, and debugging network
connectivity. A header and a data portion are both present in ICMP frame.
Message type, code, checksum, and identifier/sequence number are a few of the
fields found in the header while data portion may contain text or binary
information.
|
ICMP Type |
Function |
|
ICMP Type 8 |
Useful for network
diagnostics, including measuring the round-trip time (RTT) |
|
ICMP Type 3 |
Indication that a destination
host cannot be reached |
|
ICMP Type 11 |
Routers send this message to
let other devices know that an IP packet's Time-to-Live (TTL) value has run
out |
|
ICMP Type 5 |
Informs a host about a
different, more effective route |
DDoS:
A DDoS (Distributed Denial of Service) attack is a type of cyber attack that seeks to overload a target system, network with an influx of unauthorised traffic from multiple sources, impairing its functionality or preventing access for authorised users.
In a DDoS attack, the intention of the attacker is to overwhelm the target (i.e. record server) with many requests that its resources, such as bandwidth, processing power, or memory, are completely exhausted. The target system may experience a slowdown, become unresponsive, or even crash because of this overload. (figure 1.1)
Figure
1.1
Normal ICMP Behaviour:
Below are some common types of normal ICMP messages when network is reachable:
Figure
2.1: Normal ICMP messages in Wireshark
Herein, total 8 messages are
displayed, 4 query and reply pairs- an Echo (ping) reply for every Echo (Ping)
Request. Therefore, it ensures that the connectivity between the server and the
user is reliable where the server replies back within a given time frame.
Observations of the captured wire shark file of medical center server (Abnormal Behaviour):
Using Wireshark, I reviewed ICMP traffic from the records server. Normally, ICMP traffic includes an echo request and response pattern, as shown in Figure 2.1. However, our analysis revealed an abnormally high volume of ICMP echo requests directed at the server’s IP (200.200.1.77), coming from multiple IP addresses and with unusually brief intervals between requests. The server wasn’t responding to these echoes, further indicating an overload and potential DDoS attack, as seen in Figure 3.1.
Figure 3.1: DDoS detection by Wireshark
Explanation of the capture
file: Attack determination:
The data clearly pointed to a DDoS attack aimed at overwhelming our server with ICMP traffic, effectively blocking legitimate users and severely compromising availability—a key cybersecurity goal. This situation, defined as an “Active Attack,” involved deliberate attempts to disrupt server functionality, unlike passive attacks where data is merely observed without interference.
Analysis of the Potential
Vulnerabilities: The potential underlying causes
that may have facilitated the DDoS attack (based on the figure 3.1) would be
the social and technical vulnerabilities in the network architecture of
the St. Gabriel medical center that would include Network vulnerability, Server
vulnerability, Social - cultural vulnerability of staff as described below.
1.
Social
Vulnerabilities:
·
Inadequate
security procedures: Users frequently disregard
fundamental security procedures such as using weak passwords, failing to update
software or firmware, or failing to put the required security safeguards in
place on their devices. These flaws make equipment vulnerable to compromise and
botnet inclusion.
· IoT and Bots: The increase in the number of insecure IoT (Internet of Things) devices coupled with rise in automated bots to send echoes has led to DDoS attacks.
2. Technical Vulnerabilities
·
Software
flaws that can be exploited:
Network infrastructure with unpatched flaws can be used by attackers to
overwhelm targets and create a DDoS attacks.
·
Insufficient
network capacity and traffic management:
A DDoS attack's enormous amount of malicious traffic can overload targeted
networks or systems that are under-resourced or lack effective traffic
filtering techniques.
·
Lack of
traffic anomaly detection: It is
difficult to recognise and mitigate irregular traffic patterns linked to DDoS
attacks without efficient monitoring and detection tools.
In conclusion, these vulnerabilities may have been the subject of threats by hostile actors looking
to damage the service or reputation of the medical center. De-capacitating the server
would entail emboldening attackers and paving the way for future espionage attacks in
collaboration with DDoS, creating havoc in emergency Medicare service, threatening the
lives of vulnerable masses, sabotaging the trust people place in doctors and violating
humanity’s values.
Recommended Solutions:
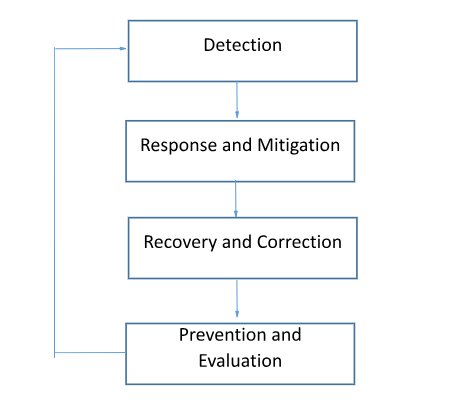
Business Continuity and Disaster Recovery Plan :
A
disaster recovery plan for a DDoS assault as shown in figure 4.1 should
include the following essential components:
1.
Detection strategy: Monitoring tools to quickly identify DDoS attacks.
2.
Response and Mitigation strategy: Establish a response strategy that
details what to do in the case of a DDoS assault, for e.g. how to alert
IT employees, get in touch with impacted users and activate DDoS Protection
Services.
3.
Recovery and Corrective Strategy: Start the process of returning to
normal operations once the assault has been contained.
5. Prevention and Evaluation strategy:
Conduct a post-incident review to find areas that may be improved and updated
upon from time to time.
Figure :4.1 Disaster Recovery Plan
|
What is DDoS Protection Services? DDoS Protection Services involves an amalgamation of Detection Prevention
and Curative Strategies implemented across the 7 layers of OSI model that
addresses the social and physical vulnerabilities of the server |
Detection
strategy:
Detective
strategy is used to investigate about the cause of the incident by analyzing
packet behaviour through the application of sniffer tools, activity log
records, etc. as explained below:
·
Signature-based
detection: By looking for recognisable
patterns or signatures in the network the method compares network
traffic to a database of recognised DDoS attack signatures. If a match is
found, the technique can intervene to stop the attack from happening by
blocking traffic coming from the attack's source.
Strengths: The
approach can be used to determine the sort of DDoS attack being utilised, which
can aid in choosing the best defences.
Weakness
of Detection: As signature-based detection may only identify
established attack patterns, it may not be effective against fresh emerging
threats that masquerade a recognizable pattern.
Attacks
that are sophisticated can utilise advanced ways to avoid being caught by this
detection measures, for instance, patterns may use encryption or look like
legal traffic.
·
Traffic
rate-based detection: This tactic entails monitoring
the flow of incoming traffic and looking out for any abrupt increases that
might be a sign of a DDoS assault.
Weakness:
Source of attacker can’t be known just by examining the traffic variations.
·
Protocol-based
detection: This method examines the protocol
being used in network traffic to find any suspicious activity that might
point to a DDoS attack. It works by inspecting the headers of network packets
to determine whether they are a part of a DDoS attack or a genuine
communication.
Strengths: The method can also be used to locate the attack's
origin, which is helpful in pursuing legal action against the offender.
Challenges with Detection Strategy: to keep up with the emerging advanced nature of DDoS
attacks, the cost of maintaining detection methods in place and keeping
them upgraded can be expensive, especially for small businesses with limited
funding.
Recovery
and Corrective Strategies:
After detecting the attack type, source, timing and causes of DDoS information,
IT administrator should resort to next stage of disaster management i.e.
corrective strategies as explained below:
- Diverting traffic
entails sending incoming traffic to a DDoS Protection Provider that uses
the cloud to filter out dangerous data.
- Filtering traffic
entails identifying and blocking harmful traffic while allowing genuine
traffic to get through using network filtering techniques. Some common
filtering techniques that could be used are:
IP
filtering, geo location filtering, protocol filtering, traffic rate filtering,
behavioral filtering.
- Rate-limiting: This can assist
prevent the network from becoming overloaded by restricting the number of
requests or connections from a single IP address or subnet. Most common
techniques used for rate limiting are as follows:
o bandwidth rate limiting that limits amount of bandwidth available for
traffic to a server.
o Connecting rate limiting: that limits the number of connections that can be
established with the server. This is achieved using firewalls, routers.
o Request rate limiting: that limits the number of requests that can be
put to a server. Its done through firewalls.
o Session rate limiting: that
limits the number of sessions that can be established to a server. This is
achieved through load balancers.
- Scaling up resources: To
manage the increased traffic load, scaling up resources entails increasing
bandwidth, processing power, or other resources. This can be achieved by
following techniques:
o Load balancers: create
multiple servers for distributing traffic.
o Cloud based solutions: such
as CDNs Content Delivery Networks can be used to distribute traffic into remote
cloud database and thus scale up server resources.
o Mirroring:
create copies of critical
hospital resources and distribute it among various servers.
- Blackholing: This method effectively shuts down the website until the attack
is over by blocking all traffic to the targeted IP address or range.
Challenges with Corrective Strategies:
- Blackholing might take a toll on center’s operations and
essential services indefinitely as one does not know till when the DDoS
attack may last.
- Mirroring, Load balancing, traffic diversion techniques are costly
adding burden to infrastructure costs of the medical center.
- The
corrective strategy is dependent upon how long it takes to detect the
problem in previous stage. Detection Latency means the delay in
implementing the corrective measures due to delays in detection of the
problem. Greg Tomsho, (2019).
Preventive
Strategy:
After
corrective strategy stage, we discuss the preventive strategy that should
be implemented to prevent such an attack happening in future.
- Use Performance Monitor Software to monitor if the
amount of available memory, processing power of server is available in
stock to support the operations. It triggers an automatic pre-emptive mail
to I.T administrator whenever an resources availability falls below a
limit.
- Server application
hardening can make a server more durable and less
vulnerable to compromise by lowering the attack surface of a server and
minimising the possibility for vulnerabilities.
- Network segmentation is a security technique that involves dividing a network into
smaller sub-networks, or segments, to reduce the impact of security
breach. It can help mitigate the impact of a DDoS attack by limiting the
spread of the attack and isolating affected systems.
- Web Content Filtering: is a security strategy that involves restricting access to web
content by preventing traffic from known malicious sources such as
well-known botnets that are frequently utilised in DDoS assaults.
- Access Control: is a
security approach that restricts access to resources based on user
identity using identity authentication. The number of people that have
access to vital resources, such as servers and databases, can be
restricted by putting access restrictions in place.
- Threat Intelligence based on adversary tradecraft
Threat Intelligence based on adversary tradecraft can certainly help prevent DDoS attacks by providing insights into the tactics, techniques, and procedures (TTPs) of potential attackers.
Final Thoughts
Working on the frontlines of cybersecurity in a healthcare setting has shown me that protecting a hospital’s digital infrastructure isn’t just about defending systems but about safeguarding the lives and trust of our community. Reflecting on this incident, it’s clear that a robust cybersecurity strategy & policy with robust documentation is need of the hour to ensure uninterrupted medical operations. By refining our response protocols and implementing preventive measures, we aim to safeguard our network infrastructure against possible future threats.
References
Belding, G. (2020, January 8). Incident response ICMP protocol with Wireshark. Infosec Resources. https://resources.infosecinstitute.com/topic/icmp-protocol-with-wireshark/
OneLogin (n.d.). What is a DDoS Attack? https://www.onelogin.com/learn/ddos-attack
Cloudflare. (n.d.). Ping (ICMP) flood DDoS attack. https://www.cloudflare.com/learning/ddos/ping-icmp-flood-ddos-attack/
Greg Tomsho Guide to Networking Essentials, 8th Edition, Chapter 14-Troubleshooting and Support, Approaches to Network Troubleshooting pg.738

Comments
Post a Comment